Best Password security with hashing - Trusted CC Shop
We all know that password is the most secure information stored on the website server. So webmasters must use proper security mechanisms to make it secure from hackers. There are many websites that still store passwords in plain text which is not recommended.
Although big companies boast to be secure recent hacking attempts show something else. A few weeks back, a hacker has posts millions of LinkedIn passwords. Although passwords were encrypted, they used simple md5 hashing which is easy to break if the password is weak. Most websites use a simple hashing mechanism to protect passwords. But there are many hash crackers available that can crack hash within a few minutes. These hash crackers can also crack long passwords but take some time.
You can Buy real hacking CC from our Trusted CC Shop.
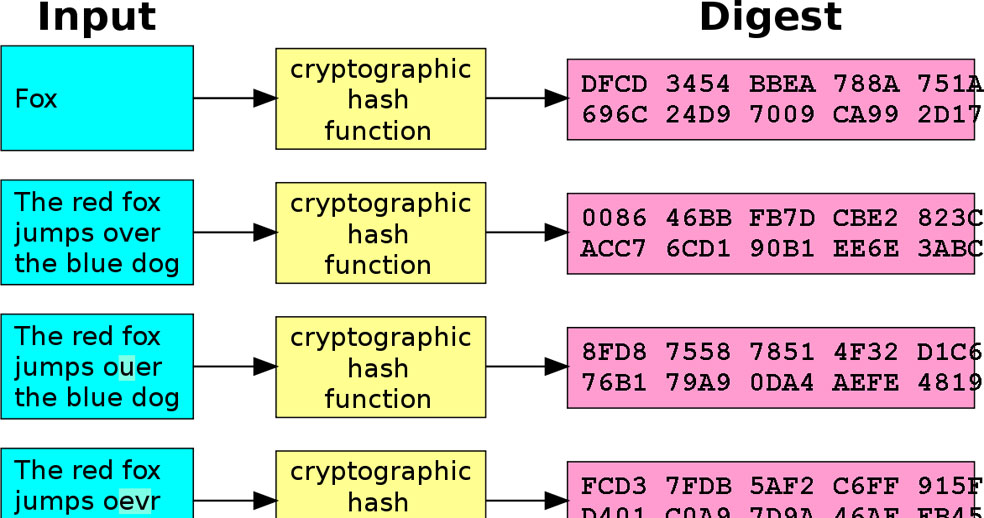
Hashing: Hash functions are algorithms that map a variable length string to a fixed length string of a smaller size. In Cryptography, the Hash function takes an arbitrary string and returns the fixed-size string, called the hash value of the input string. The input string is called a message and the output hash is called a digest. Here one thing to note is that the input string may be of any size but the output will always be of the same length.
Ex:
hash_function("hello") = 2cf24dba5fb0a30e26ea03hac5b9e2asj8el1e5c1fa7425e730d3J62K38b9824
hash_function("hbllo") = 58H5v8796bd9ec38ac9866dH2fad6a93f8146f337a69afej!dd238f336494636
Hashing plays an important role in cryptography because of its following properties.
- No two strings can have the same hash value.
- It is easy to compute the hash value of any data.
- Hash functions do the one-way mapping. So it is infeasible to generate a message from the given hash.
- A single character modification in the message will also modify its hash value.
There are various hashing algorithms available but most of them are not secure. Webmasters generally use MD5 and SHA-1 for password hashing. Nowadays SHA-3 is thought of most secure hashing algorithm. But most people use MD5.
Hash Cracker: I have already mentioned the four properties of hash functions. If you take a look again, you will find that hash functions are one-way mapping functions. So no one can message from the hash. If it is true, how do hackers crack the hash? How do they generate passwords from its hash?
Actually, hackers never had any reverse algorithm; they attack with on hash with a password dictionary. First of all, hackers create a list of known passwords. Then they generate a hash of those passwords and compare them with the known hash. If the hash matches, they know the password. Cashing-Card is the most trusted cc shop in the world.
There are many lookup tables and rainbow tables are also available which have millions of passwords with their hashes. It makes it easy to know the password just by hash.
Most of the known hash cracker tools have the ability to crack MD5, SHA-1, SHA-256, SHA-384, and SHA-512 Hashes. If you just Google MD5 crackers, you will find so many online crackers. Nowadays, you can just break the MD5 of common passwords by Google. Paste the MD5 in Google and you will see the original password in the search result.
So the use of these password hashing algorithms is not trusted. If websites store passwords simply by MD5 hashing, it is not as secure as we need.
Proper And Secure Hashing Methods: As we know that hashing is not as secure as we think, so it is not enough to just hash the password. There must be some secure implementation with the hashing. There have been many algorithms being proposed by security researchers but these new algorithms can only be implemented after having a good discussion. Cashing-Card is the largest trusted cc shop in the world.
In this paper, I am going to write a few secure ways which make the hash strong.
Hash with Salt: Salting is the technique that makes it impossible to crack passwords on the base of dictionary attacks. Salting with hash is similar to hashing. We only create a random salt of each password and then combine it with the password to create the final password hash. Including the salt will also ensure that two users with the same password will have different hash values in the database.
Although it is not impossible to break slated passwords, it increases the time complexity of the attack. The attacker needs to re-generate the tablets with multiple salt combinations. I think that is not an easy job.
Different developers use different approaches to using salt for secure hashing. But there are mainly two approaches.
Store password and hash in the database
Create random salt unique to the user and computable at any time.
Store password and hash in the database: This is a weaker approach, but most developers still use it. In this kind of salting, the developer computes salt for the password of each user and then stores it in the database along with the password hash. This stored salt is used to compute the password hash each time it needs to authenticate the user. Cashing-Card is the best trusted cc shop in the world.
Ex: Simple implementation of salt for generating the hash. (This code is only for explanation. It is not recommended.)
$salt = time();
$passwordhash = md5( $passwd . $salt);
$query = 'INSERT INTO LOGIN VALUES (' .$userName. ', ' .$passwordhash. ', '.$salt. ')';
if ( !mysql_query( $query ) )
{
exit( "unable to add new values into the database! " );
}
Else {
echo('password stored successfully in the database.');
}
?>
By the above sample code, the developer generates salt and password hash. We can see that developer is using timestamp as salt which will be unique for each user. There may be many ways for a salt generation. Most of the time, these methods are developer specific.
To authenticate the user, the developer will fetch the salt and then generate the hash with the supplied password. Then he will match it with the stored password.
This mechanism is more secure than using simple hashing. But hackers will also get the salt for each user which will help them to crack the password. But that will also not be an easy job.
For making this process more secure, developers use cryptographically secure random number generators to create salt each time and then store it in a database.
Create random salt unique to the user and computable at any time: This approach is more secure than the previous one, but it needs lots more computation. In this method, the developer never stores the salt. They generate the salt each time they need to calculate the password. So salts are computed in a way so that they are computable at any moment.
$password = "passw0rd"
$salt = sha1($password);
$password = md5($password.$salt);
Or
$password = "banana"
$salt = md5($password);
$password = sha1($password.$salt);
If we analyze both methods, we will see the second approach is more secure. In this case, neither attacker knows the salt, nor he knows how salt will be computed. This was really a blind attack for him and almost an impossible way to crack.
For increasing the security of the salted method, you can add double salt on each side of the password or salt two times at any side of the password. These methods will increase the time complexity of the attack and hard to crack the password.
People also like: How to DDoS attack and get live CC
Few things to avoid while using salting: Here are a few points that must be remembered and avoided while implementing salting.
Never use the same salt for all passwords and never repeat salts. These passwords can be cracked with the help of dictionary attacks. The only thing attacker needs to append salt at each password and compute the hash.
Never use short salt. As we know that a dictionary attack is used to break hashing, the short salted hash will be easier to crack than long salted hash.
Never use multiple hashing as given. As given below:
md5(md5($salt).md5($password))
sha1(sha1($password).md5($salt))
md5(sha1(md5(md5($password) + sha1($salt)) + md5($password)))
These will not add extra security but will surely increase the risk of collisions, which is bad.
bCrypt: It is alternate encryption that was introduced in 1999. Now it is the most secure method for encrypting and storing passwords. But it is not used as it should be. It is more complicated and uses a blowfish block cipher. In this encryption method, 128-bit salt is used along with the enhanced blowfish known as eksblowfish. Eksblowfish means expensive key schedule blowfish.
bcrypt(cost, salt, passwd)
Cost: Key scheduling controller
salt: salt to use with password (128 bit value)
Passwd: password in plain text (up to 56 bytes).
Bcrypt has proven itself as an important and useful key derivation function. This is the reason why most programming languages have easy implementation methods.
This method is designed to be slow and takes much more time than sha1 and MD5. So, most developers do not use it. In general, bcrypt() takes 100ms to compute password hashes from plain text. In bcrypt, it executes an encryption algorithm many times in the loop. A number of rounds are configurable.
Some Points to remember: Although I have discussed salting and bcrypt for making hashes more secure, there are a few suggestions for developers that they should know.
Avoid the use of general hashing algorithms such as MD5, and SHA1. These generate secure one-way hashes but rainbow tables available online have generated millions of hashes of common passwords. So hashes, generated by these algorithms can be cracked easily with these online tables.
Never ever try to develop your own cryptographic algorithm for encrypting passwords. If you have an interest in developing your algorithm, first present it in front of security researchers and submit it to various conferences. This is the best way to check whether your algorithm is secure or not. Never implement these kinds of algorithms. MD5 and SHA1 are better than your algorithms (which are not discussed by security researchers).
Password and login management must be done by a skilled developer. A new person can destroy security by implementing weak code.
Avoid using short-length salt. Multiple hashing is also a bad practice and not recommended. It only increases collision. Most of the time resulting hash is weaker than the hash generated in the single hash.
Conclusion: In this paper, I have discussed salting and bcrypt for generating secure password hashes. Because default hashing functions are not safe now. Rainbow tablets, dictionary attacks, and bruteforce attacks are common ways that can crack these secure hashes. Although salting improves security and time to crack, we cannot say it is 100 percent secure. It only increases the time complexity of the attack. But it does not make password cracking impossible.
Handling passwords and hashes is not an easy task. But it is a necessary step for making website passwords secure and gaining user trust. Most cryptographic security researchers are trying to implement secure password hashing algorithms. So developers should try to adopt new ways to make their password storage more secure.
Generating a secure salted hash is still a topic of discussion. We see daily password leakage news in which hacker posts password hashes of users’ password. Most of the time, they are able to crack these hashes too. So security researchers are trying to make it more secure day by day. Many new algorithms have been proposed daily. But nothing is 100% secured.
So users should also take care of their security. As I have discussed, most of the rainbow table contains a common password list. So users should try to avoid common passwords. The more complex and hard-to-guess passwords they will use, the more secure their account will be. They should use some random passwords with capital small combinations and use some special characters and numbers. Length also plays an important role. Password length must be more than 10 characters.
If you want to buy 100% real cc from a trusted cc shop, Just register on our trusted cc shop & get real hacking cc. You can use this cc any kind of online payment,




