Carding Tutorial
If you want to start carding. Just read our all of carding tutorial. Our tutorial help you start your carding journey.

How to Start Web Application Penetration testing With Websecurify, With - Best dumps website 2023.
If you are a developer, owner of a software firm or a testing engineer, you must know the importance of security testing. Hackers are everywhere and they always try to intrude in the system, network and applications. If we talk.........
Read More
How to password protect your computer before it even loads the operating system - best cvv shop | best cc shop 2023
Best cvv shop | best cc shop | cvv fullz:
You may like also :- validcc | ccshop | cvvshop | fullz | cc dumps | cc fullz | cvv dumps | cvv sites | validcvv | valid dumps | dump.........
Read More
cvv dump sites | central shop cvv - With Hack Paypal, Facebook, Hotmail Password Using Spy-Net RAT
Hack Paypal, Facebook, Hotmail Password Using Spy-Net RAT
As we all know, On Hacking Home we have discussed various hacking method to hack email account password. In this article, I am gonna post the most useful way on how to hack.........
Read More
Trusted cvv shop 2023 | fresh cvv | fullz dumps With How to protect your PC's from hackers
How to protect your PC's from hackers
In this day and age, where digital security is a puppet in the hands of hackers, protecting data has become a major cause of concern for IT specialists. It is, therefore, instinctive on their.........
Read More
Trace Route Tutorial - shop high balance | cc shop online | trusted cvv shop 2023
Hello reader, I was not very active for few months. I was only writing some security news, hacking and penetration tools. I know for my regular readers that was disappointing. But i was busy in establishing some of my other websites as hacking.........
Read More
Best cvv dump sites 2023 - With 5 Best Books to Learn Web Application Hacking and Penetration testing.
Year 2012 is about to end and we are waiting to celebrate new year 2013. In 2012, we have seen so many hacking incidents, data breach password leaks and website deface that belongs to popular websites. All these happens because of.........
Read More
Tips to protect Facebook account from hackers, with buying fullz | best cvv dump sites | buying cvv online for Carding.
Facebook, the social networking website or we can say our virtual world. Most of the people live more in this virtual world than their real world. We share our photos, moods and thoughts with our friends. But with the increase.........
Read More
How to Earn Legal Money By Finding Vulnerabilities
If you are hacker and know how to do penetration testing, you can earn good amount of money by your skills. many big companies have bug bounty program for security researchers. These companies invite security researchers around the world to.........
Read More
Remote computer hacking with SniperSpy
Are you looking to hack a remote computer? Do you wan to hack passwords of your friends? I am here with a leading remote computer hacking software.
SnipeSpy (Best Rated Remote hacking software)
SniperSpy is the best Remote hacking Software that.........
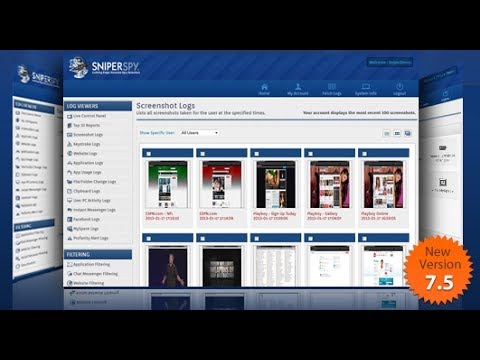
Get dumps and pins via remote computer hacking
Are you looking to hack a remote computer? Do you want to hack the passwords of your friends? I am here with a leading remote computer hacking software.
If you want to get credit card dumps and pins just register on.........
Read More
How to get live valid cc via Phishing?
When I started this security blog more than 20 months ago, I was good at hacking stuff and used to play with some common hacking methods. At that time i really enjoy phishing and trojans. Binding trojans with FUD cryptos.........
Read More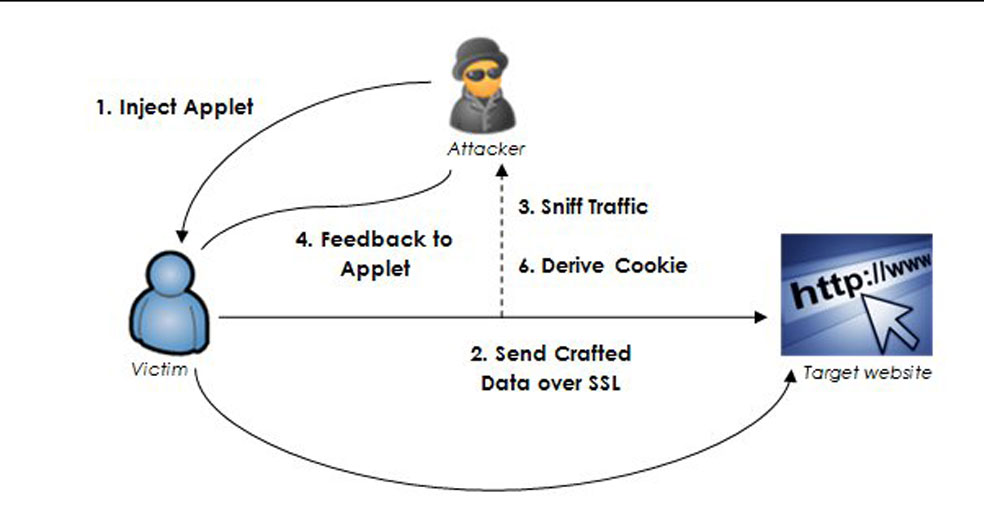
SSL websites are vulnerable to the attack & get fresh cc for carding
According to the latest cyber report by the Trustworthy Internet Movement (TIM), a nonprofit organization dedicated to solving Internet security, privacy and reliability problems, 90% of the websites running on HTTPS-enabled secure protocol are vulnerable to the SSL attack, BEAST.
This.........
Read More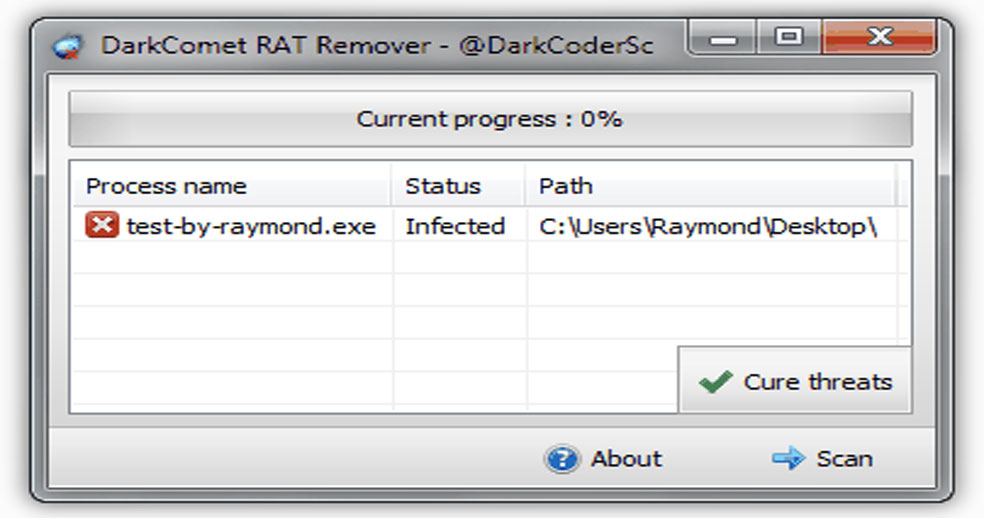
Author Terminates DarkComet RAT, Reason is misuse
Jean-Pierre Lesueur aka DarkCoderSc, developer of the most infamous RAT, DarkComet has announced that he is terminating the project. He revealed that he was getting many applications regarding the misuse of this remote administration tool (RAT).
In the past few.........
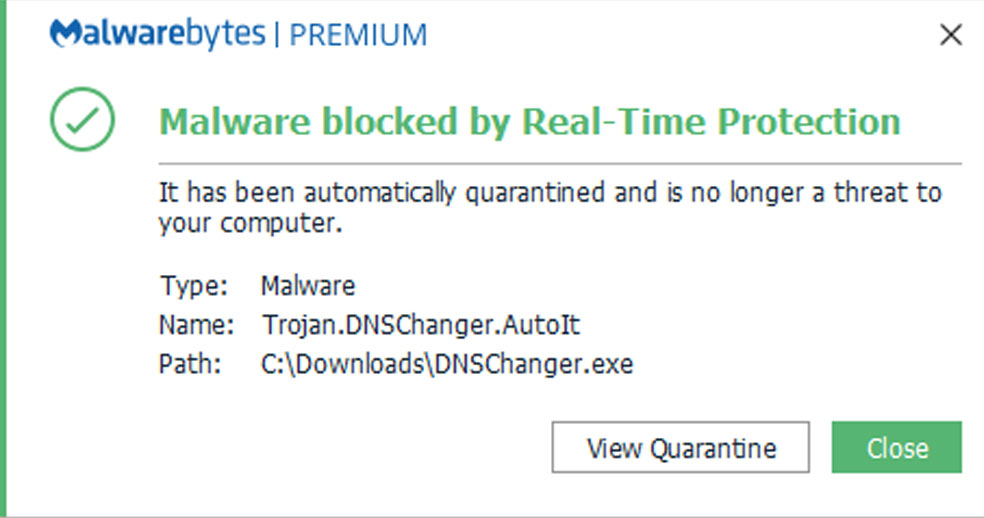
How to remove trojan DNS Changer
Yesterday, I reported that Google will warn users who are affected by the DNSChanger trojan. After the post, many readers asked me to write about this Trojan in detail. In this post, I am writing about the DNSChanger trojan.
DNSChanger is.........
Read More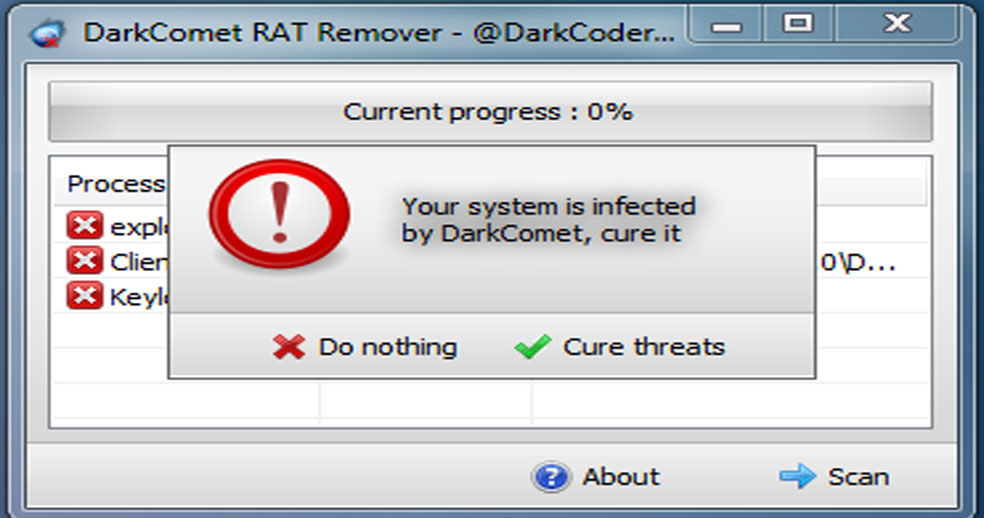
DarkComet RAT Remover Released
The developers of DarkComet RAT have released a new tool that can be used to detect and remove their own DarkComet RAT. This tool can detect any kind of instance of DarkComet running in the system even if a hacker.........
Read More
How to remove adware, trojan, spyware from the computer
Now a day, we can not think of our life without the internet. But the internet also comes with various computer threats. While we are surfing some websites, there are some possibilities that our system is getting an infection.
Your PC.........
Read More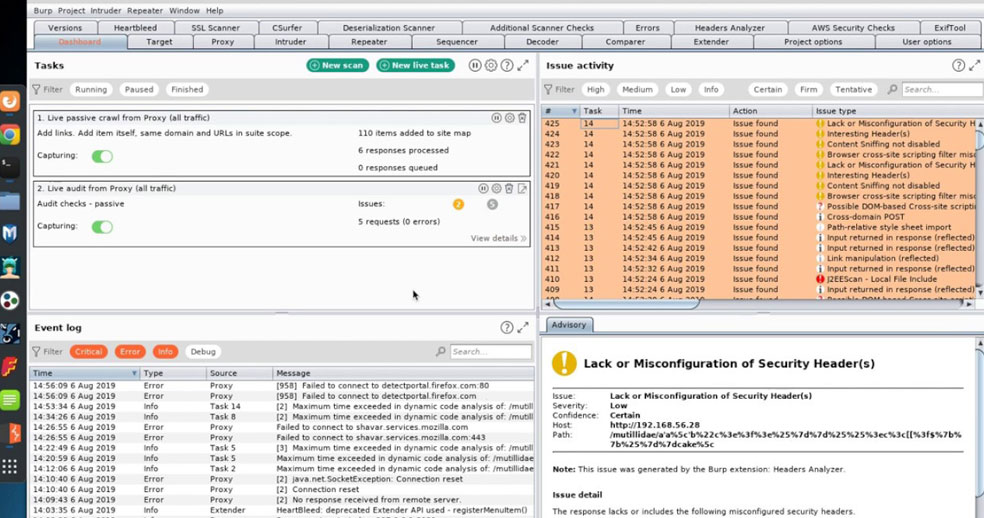
Burp Suite Web Application Testing Tool For CC Dumps
Popular web application penetration testing tool, Burp Suit has been updated. Burp Suit v1.4.10 is now available to download. This penetration testing tool analyzes web applications and finds vulnerabilities in them for cc dumps.
Now Burp Suit fully supports JSON.........

Best Spyware and Adware Removal Tool
As the use of the internet is expanding in our daily life, the use of spyware and adware is also increasing. Many internet companies use these to track browsing activities and promote some ads on the user's browser. This is.........
Read More
How to crash small websites using rDOS get Credit Card Dumps
Have you ever wanted a rDOS attack on a website for Credit Card Dumps? Here I am going to write about a tool that is really helpful but it wouldn't be effective on big servers.
NOTE: Please do not try.........

PayPal Announced Bug Bounty Program
PayPal has also announced a bug bounty program for security researchers. Security researchers will be awarded for reporting vulnerabilities that might affect Paypal and its customers.
“Today I’m pleased to announce that we have updated our original bug reporting process into.........
Read More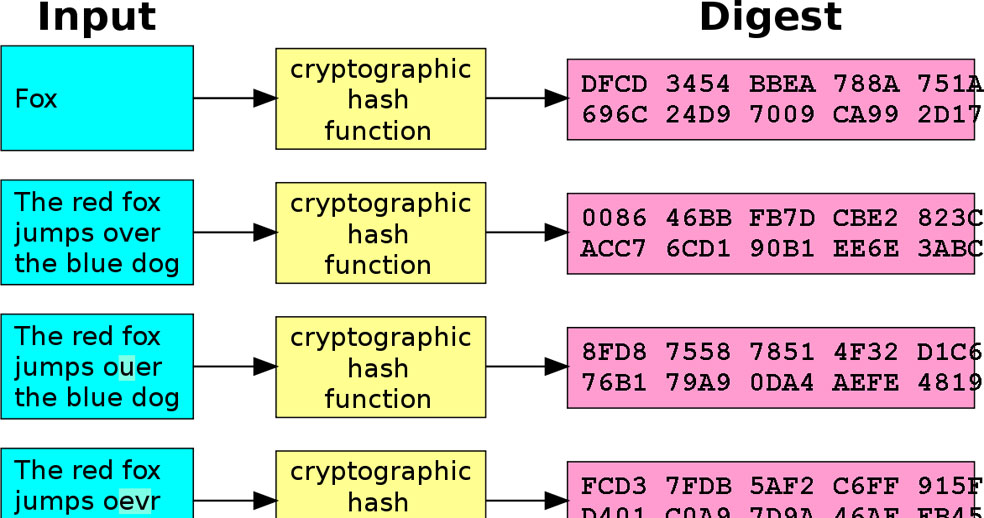
Best Password security with hashing - Trusted CC Shop
We all know that password is the most secure information stored on the website server. So webmasters must use proper security mechanisms to make it secure from hackers. There are many websites that still store passwords in plain text which.........
Read More